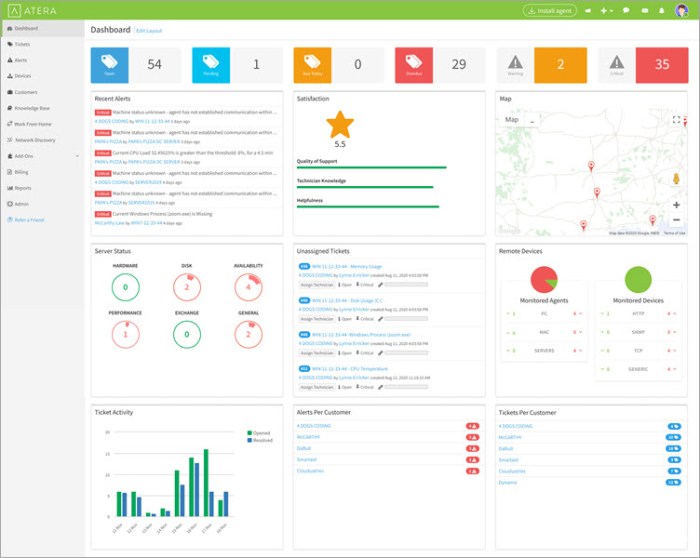
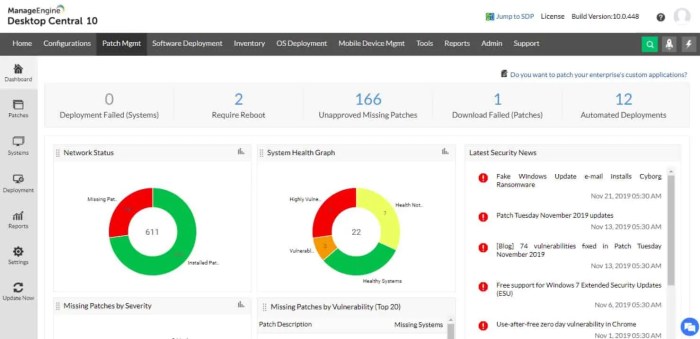
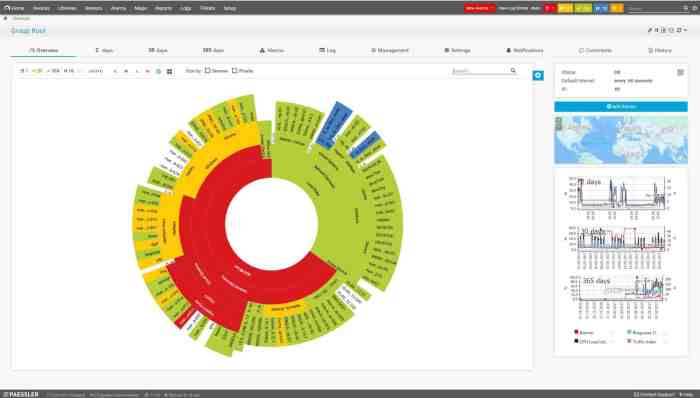
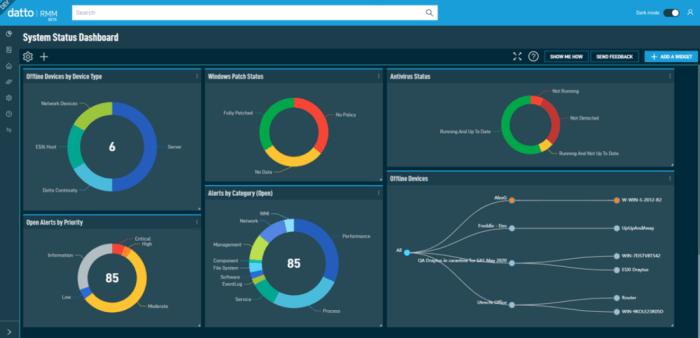
RMM software with advanced remote control and access capabilities is revolutionizing IT management. Imagine effortlessly troubleshooting a client’s computer from across the globe, securing sensitive data with multi-factor authentication, and streamlining your entire IT workflow. This isn’t science fiction; it’s the reality of modern RMM solutions. This deep dive explores the power, security, and future of advanced remote access in RMM, showing you how to leverage these tools for optimal efficiency and peace of mind.
We’ll dissect the core functionalities, comparing different methods for secure remote connections and highlighting key features that set “advanced” RMM apart from basic remote access tools. Security is paramount, so we’ll delve into best practices, including robust authentication protocols and permission management. Plus, we’ll explore integrations with other IT management tools, examine real-world case studies showcasing the benefits, and discuss the future trends shaping this dynamic landscape.
Get ready to unlock the potential of advanced remote control in your IT strategy.
Defining Advanced Remote Control and Access in RMM Software
Remote Monitoring and Management (RMM) software has evolved beyond basic remote access. Advanced capabilities are now crucial for efficiently managing IT infrastructure, providing seamless support, and ensuring robust security. This section delves into the core functionalities, crucial applications, security implications, and various connection methods of advanced remote control and access within RMM solutions.Advanced remote control in RMM software goes beyond simple screen sharing.
It empowers IT professionals with granular control over endpoints, enabling them to perform complex tasks remotely with minimal disruption. This includes functionalities like remote command execution, file transfer, registry editing, and even the ability to control multiple devices simultaneously. This level of control is essential for proactive maintenance, rapid troubleshooting, and efficient software deployment.
Core Functionalities of Advanced Remote Control
Advanced remote control within RMM solutions offers a comprehensive suite of capabilities far exceeding basic screen sharing. These functionalities enable IT administrators to perform a wide range of tasks remotely, effectively managing and maintaining endpoints without physical access. Key features include seamless remote command execution, allowing administrators to run scripts and applications on managed devices; secure file transfer for efficient deployment and retrieval of data; precise registry editing for system configuration adjustments; and the ability to control multiple devices concurrently for streamlined management of large IT infrastructures.
This level of control significantly improves operational efficiency and reduces downtime.
Scenarios Requiring Advanced Remote Control Capabilities
The advanced features of RMM remote control are not merely conveniences; they are critical in numerous situations. For instance, imagine a critical system failure at a branch office after hours. An administrator using advanced RMM can remotely diagnose the problem, execute necessary commands to restore service, and even deploy updates – all without needing to physically travel to the site.
Similarly, consider the rapid deployment of security patches across a large network. Advanced RMM allows administrators to push updates to numerous devices simultaneously, minimizing vulnerability exposure. Another scenario involves troubleshooting complex technical issues; the ability to remotely access and control system settings, files, and processes allows for faster, more efficient diagnosis and resolution.
Security Implications and Best Practices for Secure Implementation
The power of advanced remote access necessitates stringent security measures. Unauthorized access can lead to data breaches, system compromise, and significant financial losses. Implementing multi-factor authentication (MFA), strong password policies, and regular security audits are crucial. Furthermore, encryption of all data transmitted during remote sessions is paramount. Regular software updates are essential to patch vulnerabilities, and robust access control lists (ACLs) should be used to limit access to authorized personnel only.
Employing a secure VPN connection for remote access enhances security by creating a secure tunnel for all data traffic. Regular security training for IT staff is also vital to promote secure practices and prevent accidental security breaches.
Methods for Establishing Secure Remote Connections
Several methods exist for establishing secure remote connections within RMM software, each offering varying levels of security and performance. The most common approach is using Secure Shell (SSH) for secure command-line access and file transfer. SSH utilizes strong encryption to protect data during transmission. Another method involves using Virtual Network Computing (VNC) for graphical remote desktop access, though security considerations require encryption and strong authentication mechanisms.
RDP (Remote Desktop Protocol), while widely used, requires careful configuration and security measures to prevent unauthorized access. Modern RMM solutions often integrate multiple methods, allowing administrators to choose the most suitable option based on the specific task and security requirements. The choice often depends on the balance between security needs, ease of use, and performance considerations.
Key Features of RMM Software with Advanced Remote Control

RMM software offering advanced remote control capabilities goes beyond the basic functionality of simply accessing a remote device. It provides IT professionals with a comprehensive suite of tools to manage, troubleshoot, and secure endpoints efficiently, leading to significant improvements in productivity and reduced downtime. These advanced features are crucial for effectively managing increasingly complex IT environments.Advanced remote control in RMM software distinguishes itself from basic remote access through several key features.
While basic remote access might allow for simple screen viewing and control, advanced solutions offer enhanced security, automation, and granular control over multiple devices simultaneously. This level of sophistication is essential for managing diverse IT infrastructures efficiently and securely.
Technologies Enabling Advanced Remote Control
Several technologies underpin the advanced remote control capabilities found in modern RMM solutions. Remote Desktop Protocol (RDP) remains a widely used standard, offering a reliable method for accessing Windows machines. Virtual Network Computing (VNC) provides a more platform-agnostic approach, enabling control of various operating systems. However, many leading RMM providers also leverage proprietary protocols, often optimized for speed, security, and integration within their platform.
These proprietary protocols frequently incorporate advanced encryption and authentication mechanisms to safeguard sensitive data during remote sessions. The choice of technology often depends on factors such as operating system compatibility, security requirements, and the specific features offered by the RMM software.
Comparison of RMM Software Remote Control Capabilities
The following table compares the remote control capabilities of three leading RMM solutions – fictionalized for illustrative purposes – highlighting their strengths and weaknesses. Note that the specific features and performance can vary depending on the version and configuration of the software.
| RMM Software | Strengths | Weaknesses | Protocols Used |
|---|---|---|---|
| SolutiaRMM | Excellent performance, robust security features, seamless integration with other Solutia tools, supports multiple simultaneous sessions. | Can be expensive, steep learning curve for some users. | Proprietary protocol, RDP, VNC |
| ControlMax | User-friendly interface, affordable pricing, good support for a wide range of devices. | Performance can degrade with a large number of managed devices, fewer advanced features compared to SolutiaRMM. | RDP, VNC |
| RemoteAssist Pro | Strong security features, excellent scalability, advanced scripting capabilities. | Complex configuration, relatively high initial investment. | Proprietary protocol, RDP |
Security Considerations and Best Practices: RMM Software With Advanced Remote Control And Access Capabilities
Implementing RMM software with advanced remote access capabilities significantly enhances IT management efficiency, but it also introduces heightened security risks. A robust security strategy is paramount to mitigate these risks and protect sensitive data. Failing to prioritize security can lead to data breaches, system compromises, and significant financial losses. This section Artikels essential security measures and best practices for a secure RMM deployment.
Multi-Factor Authentication and Security Protocols
Multi-factor authentication (MFA) is crucial for bolstering the security of remote access. By requiring multiple forms of verification—such as a password, a one-time code from an authenticator app, and potentially biometric authentication—MFA significantly reduces the likelihood of unauthorized access, even if credentials are compromised. Other vital security protocols include Transport Layer Security (TLS) encryption for all communication channels to ensure data confidentiality and integrity, and regular security audits to identify and address vulnerabilities promptly.
Employing strong password policies, including length requirements, complexity rules, and enforced regular password changes, is also essential. Furthermore, implementing intrusion detection and prevention systems (IDPS) adds another layer of protection by monitoring network traffic for malicious activity and blocking suspicious connections.
User Permissions and Access Controls
Effective management of user permissions and access controls is fundamental to a secure RMM environment. The principle of least privilege should be strictly enforced, granting users only the necessary access rights to perform their tasks. This minimizes the potential damage from compromised accounts. Regular reviews of user permissions are necessary to ensure that access rights remain appropriate and that inactive accounts are promptly disabled.
Role-based access control (RBAC) can streamline this process by grouping users with similar roles and assigning them predefined permissions. Detailed audit logs, meticulously tracking all user activities, are indispensable for monitoring and investigating security incidents. These logs should be regularly reviewed for suspicious patterns or unauthorized access attempts.
Securing Remote Sessions and Preventing Unauthorized Access
Securing remote sessions involves a multi-layered approach. First, always utilize strong encryption protocols like TLS 1.2 or higher for all remote connections. This ensures that data transmitted between the RMM server and managed devices remains confidential and protected from eavesdropping. Regular software updates for both the RMM software and the managed devices are crucial to patch known vulnerabilities and prevent exploitation by attackers.
Learn about more about the process of What are the key features to look for when comparing different CRM systems in the field.
Implementing session timeouts automatically terminates inactive sessions, minimizing the window of opportunity for unauthorized access. Furthermore, robust access control lists (ACLs) should be configured to restrict access to specific devices and resources, preventing unauthorized users from connecting to sensitive systems. Finally, deploying network segmentation isolates sensitive systems from less critical ones, limiting the impact of a potential breach.
A step-by-step guide to securing remote sessions might involve: (1) Enabling MFA for all users; (2) Configuring TLS encryption; (3) Implementing session timeouts; (4) Regularly updating software; (5) Employing strong ACLs; (6) Regularly reviewing audit logs.
Security Checklist for RMM Implementation and Management
Prior to deploying RMM software, a comprehensive security checklist is essential. This checklist should include:
- MFA Enabled: Verify that MFA is enabled for all user accounts.
- Encryption Enabled: Confirm that strong encryption (TLS 1.2 or higher) is enabled for all communication channels.
- Regular Software Updates: Establish a schedule for regular updates of both the RMM software and managed devices.
- Access Control Lists (ACLs): Configure ACLs to restrict access to specific devices and resources.
- Session Timeouts: Implement session timeouts to automatically terminate inactive sessions.
- Regular Security Audits: Conduct regular security audits to identify and address vulnerabilities.
- Intrusion Detection/Prevention System (IDPS): Implement an IDPS to monitor network traffic for malicious activity.
- Strong Password Policy: Enforce a strong password policy with length, complexity, and regular change requirements.
- User Permission Reviews: Regularly review and update user permissions to adhere to the principle of least privilege.
- Network Segmentation: Implement network segmentation to isolate sensitive systems.
- Audit Log Monitoring: Regularly review audit logs for suspicious activity.
Integration with Other IT Management Tools

RMM software’s power extends far beyond its core remote control capabilities. Seamless integration with other IT management tools is crucial for building a truly efficient and streamlined IT infrastructure. This integration transforms disparate systems into a cohesive whole, allowing for more comprehensive monitoring, faster incident resolution, and ultimately, a significant boost in overall productivity. The benefits are particularly evident in larger organizations managing complex IT environments.Effective integration allows for automated workflows and reduced manual intervention, saving valuable time and resources.
Imagine a scenario where a system alert triggers a ticket automatically within your helpdesk system, simultaneously providing the technician with remote access to the affected device through the RMM platform. This eliminates the back-and-forth communication and manual task creation, significantly accelerating the troubleshooting process.
Integration with Ticketing Systems
Integrating RMM with a ticketing system, such as Zendesk, Jira Service Desk, or ServiceNow, creates a centralized hub for managing IT incidents. When a problem is detected, whether through automated monitoring or a user report, the RMM software can automatically generate a ticket in the chosen system, complete with relevant device information and error logs. Technicians can then access the affected machine remotely via the RMM, resolving the issue directly and updating the ticket status within the same interface.
This closed-loop system minimizes communication delays and ensures all relevant information is readily available.
Integration with Monitoring Tools
RMM’s integration with monitoring tools like Nagios, PRTG, or Datadog provides a holistic view of the IT infrastructure. Monitoring tools provide alerts on performance issues, while the RMM offers the immediate ability to remotely access and troubleshoot the problem. This combined approach enables proactive issue resolution, preventing minor problems from escalating into major outages. For example, if a server’s CPU usage consistently exceeds a predefined threshold, the monitoring tool alerts the system, and the RMM allows the technician to remotely investigate and address the root cause, perhaps by identifying and terminating resource-intensive processes.
Integration with Endpoint Detection and Response (EDR) Solutions
Integrating RMM with an EDR solution like CrowdStrike Falcon or Carbon Black strengthens security posture significantly. EDR provides advanced threat detection and response capabilities, identifying and mitigating malware before it causes widespread damage. The RMM’s remote access functionality then allows for immediate remediation, isolating infected endpoints and restoring system integrity. This combined approach offers a robust defense against cyber threats, allowing for faster incident response and minimizing the impact of security breaches.
For instance, if an EDR solution detects a ransomware attack on a workstation, the RMM can be used to immediately quarantine the machine, preventing the spread of malware to other devices on the network.
Challenges of Integrating RMM with Legacy Systems
Integrating RMM with older, legacy systems can present significant challenges. These systems often lack modern APIs or standardized communication protocols, requiring custom scripting or workarounds to achieve seamless integration. Compatibility issues, data format discrepancies, and the need for specialized expertise can increase the complexity and cost of the integration process. Thorough planning and assessment are crucial to ensure successful integration, often involving careful consideration of data migration strategies and potential compatibility limitations.
For example, an older, unsupported operating system might require significant modifications or workarounds to allow for proper RMM integration and remote control functionality.
Case Studies and Real-World Examples
Real-world applications showcase the transformative power of RMM software with advanced remote control capabilities. These case studies highlight how diverse organizations leverage these tools to enhance efficiency, bolster security, and ultimately, improve their bottom line. We’ll examine scenarios across varying IT environments, demonstrating the versatility and impact of this technology.
Case Study 1: Streamlining IT Support for a Growing SMB
Acme Corp, a rapidly expanding small-to-medium-sized business (SMB) with 50 employees, faced escalating IT support challenges. Their previous system relied heavily on on-site visits, leading to significant downtime and increased support costs. Troubleshooting issues remotely was nearly impossible due to limited access and control. Implementing an RMM solution with advanced remote control capabilities provided immediate relief. Technicians could now remotely access and troubleshoot employee computers, resolving issues quickly and efficiently.
This resulted in a 40% reduction in on-site visits, a 30% decrease in support ticket resolution time, and a measurable increase in employee productivity. The RMM software’s centralized dashboard also improved the management of software updates and security patches, significantly reducing the risk of security breaches.
Case Study 2: Enhancing Security Posture for a Large Enterprise
GlobalTech, a multinational corporation with thousands of employees across multiple locations, needed a robust solution to manage its sprawling IT infrastructure and enhance its security posture. Their previous system lacked centralized management and lacked the granularity of control needed to effectively manage remote access and security policies. By implementing an RMM solution with advanced remote control and access capabilities, GlobalTech gained centralized visibility into its entire network.
This allowed them to proactively identify and address security vulnerabilities, deploy security patches consistently, and enforce consistent security policies across all devices. The solution’s granular access control features ensured only authorized personnel could access sensitive systems, significantly reducing the risk of data breaches and unauthorized access. Furthermore, the ability to remotely wipe compromised devices minimized the impact of potential security incidents.
Case Study 3: Improving Disaster Recovery for a Healthcare Provider
HealthFirst, a regional healthcare provider, needed a reliable solution for disaster recovery and business continuity. Their previous system relied on manual backups and lacked the speed and efficiency required for rapid recovery in the event of a disaster. Implementing an RMM solution with advanced remote control allowed HealthFirst to automate backups and streamline the disaster recovery process. The ability to remotely access and control critical systems during an emergency ensured minimal disruption to patient care.
The solution’s robust reporting and monitoring capabilities provided valuable insights into system performance and potential issues, enabling proactive mitigation of risks. The ability to quickly restore systems from remote backups reduced downtime significantly, demonstrating the critical role of RMM in ensuring business continuity for this critical sector.
Summary of Case Studies, RMM software with advanced remote control and access capabilities
| Case Study | Challenge | Solution | Results |
|---|---|---|---|
| Acme Corp (SMB) | Escalating IT support costs and downtime | RMM with advanced remote control | 40% reduction in on-site visits, 30% faster ticket resolution |
| GlobalTech (Enterprise) | Lack of centralized management and security vulnerabilities | RMM with advanced remote control and granular access control | Improved security posture, reduced risk of data breaches |
| HealthFirst (Healthcare) | Inefficient disaster recovery process | RMM with automated backups and remote access | Reduced downtime, improved business continuity |
Future Trends in RMM Software Remote Access
The landscape of remote monitoring and management (RMM) software is rapidly evolving, driven by advancements in artificial intelligence, automation, and cloud computing. These emerging technologies are poised to significantly enhance the capabilities of RMM software, offering businesses unprecedented levels of control and efficiency in managing their IT infrastructure. However, these advancements also present unique challenges, requiring RMM vendors to adapt and innovate to meet the ever-changing needs of their users.The integration of AI and automation is revolutionizing remote access capabilities within RMM platforms.
This translates to more proactive, intelligent, and efficient management of IT assets.
AI-Powered Predictive Maintenance and Anomaly Detection
AI algorithms are increasingly being incorporated into RMM software to analyze vast amounts of data from managed devices, identifying potential issues before they escalate into major problems. This predictive maintenance capability allows IT teams to proactively address vulnerabilities and prevent costly downtime. For example, an AI-powered RMM system might detect a gradual increase in hard drive temperature on a server, alerting administrators to a potential failure and allowing for timely replacement, preventing data loss and service disruption.
This proactive approach contrasts sharply with traditional reactive methods, which often involve responding to problems only after they’ve already occurred.
Automated Remediation and Scripting
Automation is streamlining many aspects of remote access and control. RMM platforms are incorporating features that automate routine tasks such as software patching, security updates, and even troubleshooting common issues. This reduces the manual workload on IT staff, freeing them to focus on more strategic initiatives. Imagine a scenario where a system detects a security vulnerability; the RMM software automatically downloads and installs the necessary patch, minimizing the window of vulnerability and reducing the risk of a security breach.
This automation significantly improves response times and enhances overall system security.
Cloud-Based RMM Solutions and Enhanced Scalability
The shift towards cloud-based RMM solutions is enhancing scalability and accessibility. Cloud platforms offer increased flexibility, allowing businesses to easily scale their RMM infrastructure up or down as needed, adapting to changing demands. Furthermore, cloud-based solutions provide anytime, anywhere access to managed devices, enabling IT teams to address issues remotely regardless of their physical location. This is particularly beneficial for organizations with geographically dispersed teams or those operating in a hybrid work environment.
For instance, a global company can manage its IT infrastructure from a central location, regardless of the geographical distribution of its offices and employees. The scalability offered by cloud-based RMM allows for seamless expansion without significant infrastructure investments.
Challenges and Adaptations by RMM Vendors
The adoption of AI and cloud technologies presents challenges. Data security and privacy concerns are paramount, requiring robust security measures and compliance with relevant regulations. Furthermore, the integration of AI and automation requires careful consideration of potential biases and limitations of the algorithms used. RMM vendors are addressing these challenges by investing in advanced security features, such as encryption, multi-factor authentication, and regular security audits.
They are also focusing on developing AI algorithms that are transparent, explainable, and free from bias. Many vendors are actively incorporating features such as detailed audit trails, granular access controls, and robust data encryption to mitigate security risks and enhance user trust.
Cost and ROI of Advanced RMM Solutions
Investing in advanced Remote Monitoring and Management (RMM) software is a strategic decision for any IT department, balancing immediate costs against long-term benefits. Understanding the pricing models and calculating the return on investment (ROI) is crucial for justifying the expense to stakeholders and ensuring a successful implementation. This section breaks down the typical costs and provides a framework for calculating and demonstrating ROI.
The cost of advanced RMM solutions varies significantly depending on several factors including the number of devices managed, the specific features required, the level of support offered by the vendor, and the chosen licensing model. Generally, pricing structures are tiered, with higher tiers offering more advanced features and support.
Pricing Models for Advanced RMM Software
RMM vendors typically offer different pricing models, each with its own advantages and disadvantages. Understanding these models is key to selecting the best fit for your organization’s needs and budget.
- Per-device pricing: This model charges a fee for each device managed by the RMM software. The cost per device usually decreases as the number of devices increases.
- Per-technician pricing: This model charges a fee based on the number of technicians who will use the software. This is suitable for organizations with a small number of devices but a larger IT team.
- Subscription-based pricing: This is a common model where organizations pay a recurring monthly or annual fee for access to the software and its features. This often includes updates and support.
- Custom pricing: For larger enterprises with complex needs, vendors often offer customized pricing packages that reflect the organization’s specific requirements.
Calculating the Return on Investment (ROI) for Advanced RMM
Calculating the ROI of an advanced RMM solution requires a careful assessment of both costs and benefits. A simplified ROI calculation can be expressed as follows:
ROI = (Net Benefits – Total Costs) / Total Costs
Net Benefits include reduced IT support costs (e.g., fewer on-site visits, faster troubleshooting), increased efficiency, improved security, and minimized downtime. Total Costs include the initial software license fees, implementation costs, training expenses, and ongoing maintenance fees.
For example, consider a company that spends $10,000 annually on reactive IT support. Implementing an RMM solution costing $5,000 annually that reduces support costs by 50% would yield a net benefit of $5,000 ($10,000/2). Using the ROI formula: (5000-5000)/5000 = 0 or 0%. However, if the RMM solution also prevented a major system outage that would have cost $20,000, the net benefit increases significantly, resulting in a positive ROI.
Justifying the Cost of Advanced RMM Software to Stakeholders
To effectively justify the cost of advanced RMM software to stakeholders, focus on quantifiable benefits and demonstrate a clear return on investment. Presenting the information in a clear and concise manner is vital.
- Quantify cost savings: Show how the RMM solution will reduce costs associated with IT support, help desk calls, and on-site visits.
- Highlight increased efficiency: Demonstrate how the software will improve technician productivity, allowing them to manage more devices and resolve issues more quickly.
- Emphasize improved security: Explain how the RMM solution’s security features will protect the organization from cyber threats and data breaches.
- Showcase minimized downtime: Illustrate how proactive monitoring and automated alerts will prevent costly system outages.
- Develop a comprehensive ROI analysis: Present a detailed analysis showing the projected return on investment, considering both costs and benefits.