Powerful RMM software offering comprehensive network monitoring tools is no longer a luxury; it’s a necessity. In today’s interconnected world, businesses rely heavily on their networks, making robust monitoring crucial for efficiency, security, and overall success. This deep dive explores the key features, benefits, and considerations when selecting a powerful RMM solution equipped with advanced network monitoring capabilities.
We’ll unpack everything from automation and security features to reporting, scalability, and user experience, ensuring you’re well-informed to make the right choice for your organization.
Choosing the right RMM software is a significant decision, impacting everything from IT operational efficiency to overall network security. This article will guide you through the essential aspects to consider, helping you navigate the complexities of RMM solutions and select the one that best fits your needs. We’ll examine the functionalities that differentiate powerful RMM from basic options, emphasizing the importance of features like comprehensive network monitoring, automation, robust security, and intuitive reporting.
Defining Powerful RMM Software
Powerful RMM (Remote Monitoring and Management) software goes beyond basic remote access and control. It offers a comprehensive suite of tools designed to proactively manage and secure an organization’s IT infrastructure, boosting efficiency and minimizing downtime. Instead of simply reacting to issues, powerful RMM allows for predictive maintenance and streamlined workflows, ultimately improving overall IT health.Powerful RMM software distinguishes itself from basic solutions through its depth of features, scalability, and advanced automation capabilities.
Basic RMM might offer remote control and basic monitoring, but powerful RMM integrates advanced security features, extensive reporting, and automation capabilities to handle complex IT environments efficiently. This translates to a significant reduction in manual tasks and improved response times to potential problems.
Key Features of Powerful RMM Software
Powerful RMM software incorporates a range of features designed to streamline IT management and enhance security. These features work together to provide a holistic approach to IT operations. For example, robust patch management prevents vulnerabilities before they can be exploited, while advanced reporting provides actionable insights into network performance and security posture. The combination of these features creates a significantly more powerful and effective solution than basic RMM tools.
Advanced Automation Capabilities
A defining characteristic of powerful RMM is its ability to automate numerous IT tasks. This includes automated patching, software deployment, and even proactive alerts based on predefined thresholds. For instance, if a server’s CPU utilization consistently exceeds 90%, the system could automatically trigger an alert, allowing IT staff to address the issue before it impacts performance. This proactive approach, enabled by automation, is a key differentiator.
Without automation, such constant monitoring would require significant manual effort.
Comprehensive Network Monitoring
Powerful RMM software provides in-depth network monitoring capabilities, extending beyond basic metrics. It offers real-time visibility into network traffic, bandwidth usage, and device performance. For example, the software might detect anomalies in network traffic patterns, indicating a potential security breach or performance bottleneck. This level of granular monitoring allows for proactive identification and resolution of network issues, preventing disruptions and maintaining optimal performance.
This is in stark contrast to basic solutions that offer only a limited view of network health.
Advanced Security Features
Beyond basic antivirus, powerful RMM incorporates advanced security features such as vulnerability scanning, endpoint detection and response (EDR), and security information and event management (SIEM) integration. This multi-layered approach ensures comprehensive protection against cyber threats. For example, vulnerability scanning identifies software weaknesses, allowing for timely patching and preventing exploitation. EDR provides real-time monitoring of endpoints for malicious activity, allowing for rapid response to security incidents.
The integration with SIEM tools allows for centralized security event management and reporting. This comprehensive approach to security is absent in basic RMM solutions.
Scalability and Flexibility
Powerful RMM solutions are designed to scale with the growth of an organization’s IT infrastructure. They can easily accommodate an increasing number of devices and users without compromising performance or functionality. This scalability is crucial for organizations that anticipate growth or have geographically dispersed locations. The ability to adapt to changing needs distinguishes powerful RMM from solutions that are limited in their capacity.
Comprehensive Network Monitoring Tools within RMM
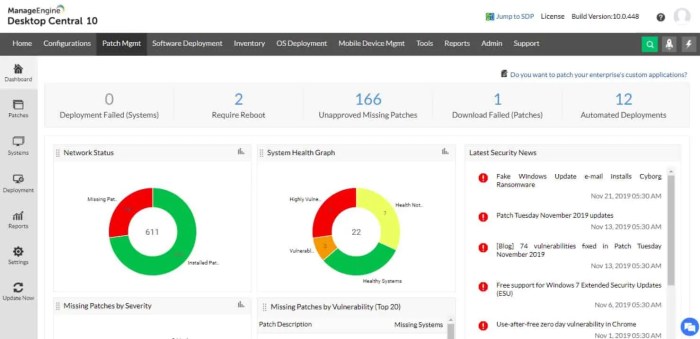
Powerful RMM (Remote Monitoring and Management) software goes beyond basic device management; it provides comprehensive network monitoring capabilities crucial for maintaining a secure and efficient IT infrastructure. This allows IT teams to proactively identify and address potential issues before they impact productivity and security. Understanding the essential components and benefits of these tools is key to selecting the right RMM solution for your needs.Network monitoring within an RMM platform is not merely about checking if devices are online.
It’s about gaining deep visibility into network performance, security posture, and overall health. This allows for proactive problem-solving, reducing downtime and enhancing security. A robust RMM solution provides a centralized dashboard, offering a single pane of glass view of the entire network.
Essential Components of Comprehensive Network Monitoring
A truly comprehensive network monitoring system within an RMM platform includes several key components working in synergy. These components provide a holistic view of network performance and security. Missing even one can significantly limit the effectiveness of the entire system.These components ensure that IT administrators have the tools they need to monitor, analyze, and address network-related issues effectively and efficiently, leading to significant improvements in both security and operational efficiency.
Network Monitoring Tools and Their Impact on Network Security and Operational Efficiency
The integrated network monitoring tools within a powerful RMM solution significantly enhance both network security and operational efficiency. Real-time monitoring allows for the immediate detection of anomalies, such as unauthorized access attempts or performance bottlenecks. This proactive approach minimizes the impact of security breaches and operational disruptions.Improved network security comes from the ability to identify and respond to threats quickly.
Operational efficiency is boosted through the reduction of downtime and the simplification of troubleshooting processes. The centralized dashboard provides a single source of truth, eliminating the need to juggle multiple tools and reports.
Comparison of Network Monitoring Capabilities Across RMM Solutions
The following table compares the network monitoring capabilities of three hypothetical RMM solutions – Solution A, Solution B, and Solution C – showcasing the variation in features, performance, and scalability. Remember that specific features and performance will vary depending on the vendor and the specific version of the software.
| Features | Solution A | Solution B | Solution C |
|---|---|---|---|
| Real-time bandwidth monitoring | Yes | Yes | Yes |
| Network device discovery and mapping | Yes | Yes | Yes |
| Alerting and notifications (email, SMS) | Yes | Yes | Yes |
| Performance metrics (latency, packet loss) | Basic | Advanced | Advanced |
| Security event logging and analysis | Limited | Comprehensive | Comprehensive |
| Network traffic analysis | No | Yes | Yes |
| Scalability (number of devices managed) | Small to Medium | Medium to Large | Large |
| Integration with other security tools | Limited | Good | Excellent |
| Reporting and analytics | Basic | Advanced | Advanced, with custom dashboards |
Integration and Automation Capabilities
In today’s fast-paced IT landscape, efficient network management is paramount. Powerful RMM software isn’t just about monitoring; it’s about seamlessly integrating with your existing tools and automating repetitive tasks, freeing up your team to focus on strategic initiatives. The ability to integrate and automate is no longer a luxury—it’s a necessity for maintaining a robust and responsive IT infrastructure.Seamless integration with other IT management tools is crucial for a holistic view of your network health.
Imagine trying to piece together information from disparate systems—a ticketing system, a help desk solution, and your RMM platform. It’s a recipe for inefficiency and missed alerts. A powerful RMM solution should act as a central hub, consolidating data from various sources and presenting a unified dashboard for comprehensive network oversight. This integration minimizes data silos, enabling faster incident response and proactive problem resolution.
Automation features further enhance this efficiency by reducing manual intervention, leading to significant cost savings and improved overall productivity.
Automated Patch Management
Automated patch management is a game-changer. Instead of manually deploying updates across hundreds of devices, a robust RMM solution can automatically scan for vulnerabilities, download the necessary patches, and deploy them at scheduled times, minimizing downtime and securing your network against potential threats. This automation ensures consistent patching across your entire infrastructure, significantly reducing your attack surface and compliance risks.
For instance, imagine the scenario of a critical zero-day vulnerability being discovered. With automated patch management, the RMM can automatically deploy the patch, mitigating the risk before a potential breach occurs. This proactive approach is far more efficient than relying on manual processes which can easily fall behind schedule.
Automated Alerting and Ticketing
Proactive alerting and automated ticket creation streamline incident response. When a critical threshold is breached—high CPU usage, disk space nearing capacity, or a network outage—the RMM automatically generates alerts, notifying the appropriate personnel. Furthermore, it can automatically create tickets in your help desk system, complete with relevant details, ensuring a swift and organized response. This eliminates the manual process of monitoring dashboards, identifying issues, and creating tickets, freeing up valuable time for more complex tasks.
For example, if a server experiences a sudden spike in CPU usage, the RMM can automatically trigger an alert, create a ticket in your help desk system, and even automatically initiate a reboot if configured, minimizing downtime and ensuring a quick resolution.
Automated Backups and Recovery
Data loss can be catastrophic. A powerful RMM solution offers automated backup and recovery capabilities, ensuring business continuity. By automatically backing up critical data at scheduled intervals, the RMM safeguards against data loss due to hardware failure, ransomware attacks, or human error. In case of a disaster, the automated recovery features allow for quick restoration, minimizing downtime and data loss.
This automation is crucial for businesses of all sizes, providing peace of mind and ensuring business resilience. Consider a scenario where a ransomware attack encrypts critical files. With automated backups, the RMM can quickly restore the affected data from a clean backup, minimizing the impact of the attack and reducing recovery time.
- Scenario: Automated software updates. Benefit: Reduced vulnerability exposure and improved security posture.
- Scenario: Automated hardware monitoring and alerting. Benefit: Proactive identification and resolution of hardware issues, preventing potential outages.
- Scenario: Automated remote control and troubleshooting. Benefit: Faster resolution of user issues and reduced on-site visits.
- Scenario: Automated report generation. Benefit: Improved visibility into network performance and compliance status.
Security Features and Threat Detection
Powerful RMM software goes beyond basic network monitoring; it incorporates robust security features to proactively identify and mitigate potential threats. These features are crucial in today’s increasingly complex cyber landscape, providing businesses with a critical layer of defense against malware, ransomware, and other sophisticated attacks. The integrated nature of these security tools within the RMM platform allows for efficient management and streamlined responses.The proactive nature of these security features is a key differentiator.
Instead of simply reacting to incidents, RMM software with strong network monitoring capabilities can predict and prevent problems before they escalate. This predictive capability significantly reduces downtime and minimizes the impact of security breaches. By continuously monitoring network activity and system behavior, these platforms can identify anomalies and potential vulnerabilities, allowing for timely intervention and preventative measures.
Vulnerability Scanning and Patch Management
RMM software offers automated vulnerability scanning, identifying weaknesses in systems and applications that could be exploited by attackers. This involves regularly checking for known vulnerabilities in operating systems, software, and firmware. The integrated patch management capabilities then automatically deploy security updates and patches to remediate identified vulnerabilities, significantly reducing the attack surface. For example, a vulnerability scan might reveal an outdated version of a web server software with known exploits; the RMM system would then automatically deploy the latest security patch to eliminate the risk.
Intrusion Detection and Prevention
Advanced RMM solutions incorporate intrusion detection and prevention systems (IDPS). These systems monitor network traffic and system activity for malicious behavior, such as unauthorized access attempts, malware infections, and data exfiltration. Upon detecting suspicious activity, the IDPS can trigger alerts, block malicious traffic, and automatically take corrective actions, such as quarantining infected devices. Imagine a scenario where an employee’s workstation is compromised by ransomware; the IDPS would detect unusual network activity, isolate the infected machine, and prevent the ransomware from spreading to other systems.
Endpoint Security and Anti-Malware, Powerful RMM software offering comprehensive network monitoring tools
Many RMM platforms integrate endpoint security features, including real-time anti-malware protection. This ensures that all managed devices are protected against malware, viruses, and other threats. These integrated security tools often include features like behavioral analysis, sandboxing, and machine learning to detect even sophisticated zero-day threats. For instance, if a new and unknown piece of malware attempts to execute on a managed endpoint, the anti-malware component will detect and neutralize it before it can cause harm.
Security Information and Event Management (SIEM) Integration
Some advanced RMM platforms offer integration with SIEM systems, providing a centralized view of security events across the entire IT infrastructure. This allows for more comprehensive threat detection and incident response. By correlating security logs from various sources, SIEM integration helps identify patterns and trends that might indicate a larger security breach or ongoing attack. A SIEM-integrated RMM system can, for instance, correlate a suspicious login attempt detected on a server with a malware infection on a workstation, providing a complete picture of the incident.
Discover the crucial elements that make The impact of HRIS on employee self-service and satisfaction the top choice.
Comparison of Security Features in Top RMM Solutions
The following table compares the security features of three leading RMM solutions (fictionalized for illustrative purposes):
| Feature | Solution A | Solution B | Solution C |
|---|---|---|---|
| Vulnerability Scanning | Automated, scheduled scans; extensive vulnerability database | Automated scans; limited vulnerability database | Manual scans only; limited database |
| Patch Management | Automated patching with approval workflows; extensive patch library | Automated patching; limited patch library | Manual patching only |
| Intrusion Detection/Prevention | Integrated IDPS with real-time threat detection and response | Basic intrusion detection; limited response capabilities | No integrated IDPS |
| Endpoint Security | Integrated anti-malware, behavioral analysis, and endpoint detection and response (EDR) | Basic anti-malware; no EDR | No integrated endpoint security |
Reporting and Analytics: Powerful RMM Software Offering Comprehensive Network Monitoring Tools
Powerful RMM software goes beyond basic monitoring; it provides in-depth reporting and analytics crucial for proactive IT management. These capabilities offer actionable insights into network performance, security posture, and overall system health, enabling IT teams to optimize resource allocation and prevent potential issues before they impact users. The right reporting tools translate raw data into easily digestible information, empowering informed decision-making.Data-driven insights are the key to efficient IT management.
Effective reporting and analytics within an RMM solution translate complex network data into clear, actionable information, allowing IT teams to identify trends, pinpoint problem areas, and proactively address potential issues. This proactive approach significantly reduces downtime, improves network security, and optimizes overall IT efficiency. The reports generated should be customizable and easily exportable, allowing for diverse uses across the organization.
Network Performance Reports
Comprehensive network performance reports should include metrics like bandwidth usage, latency, packet loss, and CPU/memory utilization across all monitored devices. These reports can highlight potential bottlenecks, such as overloaded servers or congested network segments, allowing for targeted optimization efforts. For instance, a report might reveal consistently high latency on a specific server, indicating a need for hardware upgrades or application optimization.
The ability to drill down into individual devices and applications provides even greater granularity for troubleshooting.
Security Vulnerability Reports
Security is paramount, and a powerful RMM solution provides detailed reports on identified vulnerabilities. These reports should list discovered vulnerabilities, their severity levels (critical, high, medium, low), and recommended remediation steps. The system should also track the patching status of critical vulnerabilities, ensuring that security measures are implemented promptly. A well-structured report might include a table summarizing vulnerabilities, their CVSS scores, affected devices, and the status of patching efforts.
Customizable Reporting and Dashboards
The ability to customize reports and create personalized dashboards is a crucial feature. IT teams should be able to select specific metrics, devices, and timeframes for reporting. This allows them to focus on the most relevant information and track key performance indicators (KPIs) relevant to their specific needs. For example, a dashboard might display real-time bandwidth usage, critical alerts, and the overall security posture of the network, providing a high-level overview of the IT environment.
Example of a Comprehensive Report
The following example illustrates a section of a comprehensive report detailing network performance metrics and security vulnerabilities. Note that the specific data structure may vary depending on the RMM software used. "reportDate": "2024-10-27", "networkPerformance": "bandwidthUsage": "total": "1.5Gbps", "peak": "1.2Gbps", "average": "800Mbps" , "latency": "average": "20ms", "highest": "50ms", "device": "Server_01" , "packetLoss": "rate": "0.5%", "location": "NetworkSegment_A" , "cpuUtilization": "server_01": "85%", "server_02": "60%", "server_03": "30%" , "securityVulnerabilities": [ "vulnerabilityID": "CVE-2024-XXXX", "severity": "Critical", "affectedDevice": "Server_01", "remediationStatus": "Pending" , "vulnerabilityID": "CVE-2024-YYYY", "severity": "High", "affectedDevice": "Workstation_03", "remediationStatus": "Patched" ]
User Experience and Interface Design
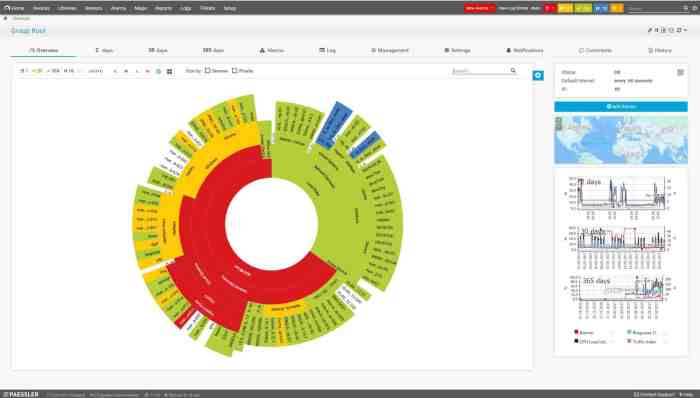
Powerful RMM software isn’t just about robust features; it’s about how easily those features can be accessed and utilized. A clunky interface can negate the benefits of even the most advanced technology, turning a potentially streamlined workflow into a frustrating ordeal. The ideal RMM solution prioritizes intuitive design, making complex tasks manageable for users of all technical skill levels.A positive user experience hinges on seamless navigation and clear visual communication.
This means a well-structured layout, consistent design elements, and the strategic use of color and typography to guide the user’s eye and highlight important information. The software should feel responsive and efficient, with minimal loading times and smooth transitions between screens. Think of it like a well-designed app – intuitive, easy to learn, and a pleasure to use.
Dashboard Design and Key Performance Indicators
The dashboard serves as the central hub, providing a snapshot of the entire network’s health and performance. An ideal dashboard presents key performance indicators (KPIs) in a clear, concise, and visually appealing manner. Imagine a dashboard with easily digestible charts and graphs displaying critical metrics such as the number of active alerts, overall system uptime, and the number of devices requiring attention.
Color-coding can further enhance readability, with green indicating healthy systems, yellow for warnings, and red for critical alerts. Each KPI should be accompanied by a brief description, providing context and allowing for quick identification of potential problems. For instance, a section displaying “Critical Alerts” might highlight specific devices experiencing issues, with clickable links to detailed diagnostics. Another section could display a graph charting network uptime over the past 24 hours, allowing for immediate identification of potential outages or performance dips.
Finally, the dashboard should be customizable, allowing users to select and prioritize the KPIs most relevant to their specific needs and workflows. This personalized approach enhances efficiency and ensures that critical information is readily accessible.
Scalability and Cost-Effectiveness
Choosing the right RMM software is a crucial decision for any business, especially considering the long-term implications. A powerful solution needs to not only meet current needs but also adapt to future growth and evolving technological landscapes. This necessitates a deep dive into the crucial aspects of scalability and cost-effectiveness. Ignoring these factors can lead to significant financial burdens and operational inefficiencies down the line.Scalability in an RMM solution refers to its ability to handle increasing workloads and user demands without compromising performance or functionality.
As your business expands, so too will your IT infrastructure and the number of devices requiring management. A scalable RMM solution seamlessly accommodates this growth, preventing bottlenecks and ensuring consistent, reliable performance. This is especially important for businesses anticipating rapid expansion or those experiencing unpredictable spikes in activity. For example, a seasonal retail business might see a dramatic increase in devices needing management during peak periods; a scalable RMM solution would handle this without issue, unlike a less flexible system which might struggle to cope, leading to performance degradation and potentially impacting customer service.
Pricing Models and Long-Term Costs
Understanding the various pricing models available is vital for making an informed decision. Different RMM vendors offer diverse approaches, impacting overall cost over time. Careful consideration of these models is essential to prevent unexpected expenses and ensure the chosen solution aligns with the business’s budget.
| Pricing Model | Description | Advantages | Disadvantages |
|---|---|---|---|
| Per-Device | Charges are based on the number of devices managed. | Simple to understand and budget for, transparent pricing. | Can become expensive as the number of devices increases significantly; less attractive for businesses with rapidly expanding IT infrastructure. |
| Per-Technician | Charges are based on the number of technicians using the software. | Cost-effective for businesses with a small IT team managing a large number of devices. | Can be less transparent if the team size fluctuates; may not be ideal for businesses outsourcing IT management. |
| Tiered/Subscription-Based | Offers different packages with varying features and device limits at different price points. | Provides flexibility to choose a plan that best suits current needs, with potential for upgrades as requirements change. | Requires careful evaluation of features included in each tier to avoid overspending or underutilizing the software. |
| Custom/Enterprise | Tailored pricing plans designed for large organizations with specific needs and complex IT environments. | Provides highly customized solutions and dedicated support. | Often requires extensive negotiations and may have higher upfront costs. |